What Is SonicWall Advanced Protection?
SonicWall Advanced Protection (aka; SonicWall TotalSecure – Advanced Edition) extends enterprise-grade security to small businesses and branch offices – and even home offices – by enabling advanced cloud security and management features. With the release of SonicWall’s Generation 7.0 TZ firewalls and the SonicOS 7 operating system, even desktop firewalls are able to deploy advanced security services. These new models feature modernized user interfaces, integrated SD-WAN, and cloud-based management in several new TotalSecure suites.







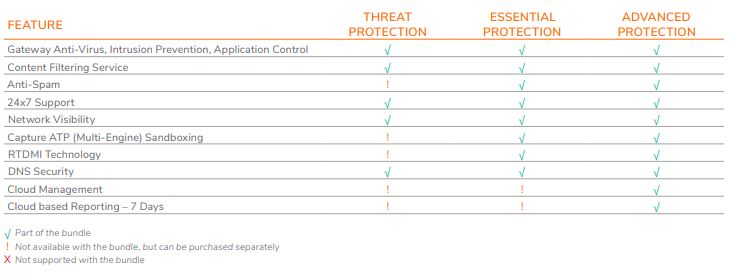
Bundle your new hardware with the basic Threat Protection suite, the Essential Protection suite, or the Advanced Protection suite to make the most out of your security investment. This article cracks open the beefiest of these new TotalSecure bundles to examine what services are included in the SonicWall Advanced Protection suite.

SonicWall Advanced Protection Suite
The SonicWall Advanced Protection suite (available in the TotalSecure – Advanced Edition bundle) includes:
Gateway Anti-Virus & Anti-Spyware
Stop viruses and spyware with real-time scanning and multi-layered protection through the Reassembly Free Deep Packet Inspection (RFDPI) engine. The RFDPI engine scans all inbound, outbound, and intra-zone traffic for viruses, Trojans, key loggers, and other malware in files of unlimited length and size across all ports and TCP streams. Block advanced threats with machine learning and a worldwide network of security sensors that are constantly updating a cloud database of millions of threat signatures. On top of that, SonicWall Capture Client uses static AI engines to determine threats before they have an opportunity to execute.
Intrusion Prevention Service
Prevent outside threat actors from setting foot in your network! SonicWall IPS blocks malicious worms and remote code execution. It also bolsters your security by segmenting networks into individual security zones to stop threats from propagating across zone boundaries.







Content Filtering
Want to block Netflix, Facebook, YouTube, and gaming sites from your network? Deny access to illegal, unproductive, and/or inappropriate sites by filtering content based on users, devices, groups, or time of day. Enforce acceptable use policies and block access to both HTTP and HTTPS websites containing content deemed objectionable.
24×7 SonicWall Support
Ensure you’re always armed with the latest firmware updates. Plus, get unfettered access to an intuitive web portal for round-the-clock support from the SonicWall team.
Capture Advanced Threat Protection
SonicWall Capture ATP is a multi-engine, cloud-based sandbox solution that prevents unknown attacks and advanced threats like ransomware and encrypted malware. Capture ATP even offers automated remediation and damage rollback in case of a breach.
Basic DNS Security
Provide authentication for the origin of Domain Name Service (DNS) data to safeguard against dangerous web content. Basic DNS protection adds a substantial layer of defense between your employees and the public Internet.
Network Topology with Host Info
Increased visibility lets network administrators monitor and control traffic at a granular level, leaving no doubt about whether your network is secure. Display hosts, access-points connected in a user’s network based on device name, mac addresses, IP addresses, and more.
Real-Time Deep Memory Inspection
Real-Time Deep Memory Inspection (RTDMI) detects malware and zero-day threats by inspecting directly in memory, offering analysis of every bit of network traffic in real time without adding latency.
Cloud Management & Reporting
The era of digital transformation is upon us and small businesses are ready to upgrade their cloud infrastructure. SonicWall cloud management allows admins to manage firewalls through the cloud via Network Security Manager or Capture Security Center. Plus, Network Security Manager Essentials, included with SonicWall Advanced Protection, features seven days of cloud-based reporting to easily analyze and understand how your network is performing.
Which Firewalls Offer SonicWall Advanced Protection?
SonicWall TotalSecure Advanced Protection (Note: For non-Gen 7 TZ Firewalls, TotalSecure Advanced Edition still refers to Advanced Gateway Security Suite) rolled out with SonicOS 7 and, as such, is only supported on Gen 7 SonicWall firewalls. This generation includes the SonicWall TZ270, TZ370, TZ470, TZ570, and TZ670. SonicWall Advanced Protection will also be available on the SonicWall NSa 2700 when it is released in late 2020 or early 2021. And a final note, the basic Threat Protection bundle is only available on the TZ270, TZ370, & TZ470.